Skip to the content
The BPO sector is currently under attack by a cybercrime group known as Muddled Libra, which employs sophisticated social engineering tactics to gain unauthorized access. […]
June 24, 2023
In the realm of cybersecurity, intrusion detection and prevention systems (IDS/IPS) are paramount in safeguarding against threats that manage to slip past endpoint and perimeter […]
April 12, 2023
Arkime, formerly known as Moloch, is a powerful tool for full packet capture and analysis. It offers a wide range of features that make it […]
March 29, 2023
Kali Linux 2023.1 is a popular Linux distribution that is used by security professionals and hackers alike to test the security of computer systems and […]
March 29, 2023
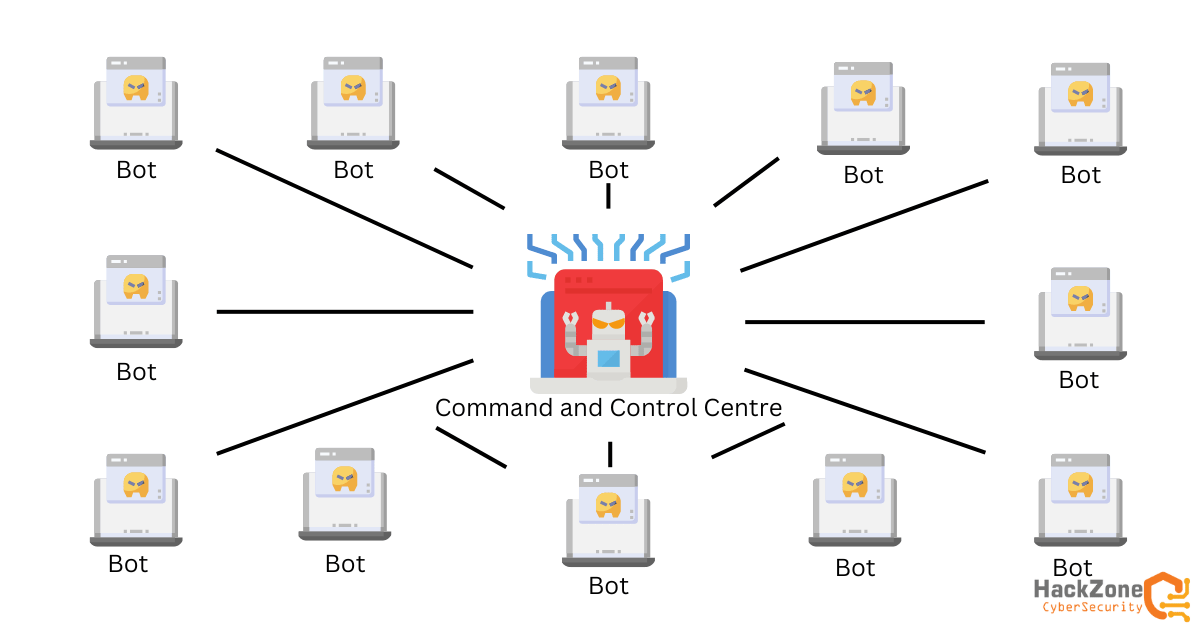
BitSight, a cybersecurity company, has revealed that a sophisticated botnet called MyloBot has affected thousands of systems across the globe. Most of the compromised systems […]
March 7, 2023
We use cookies in order to give you the best possible experience on our website. By continuing to use this site, you agree to our use of cookies.