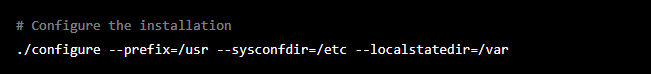
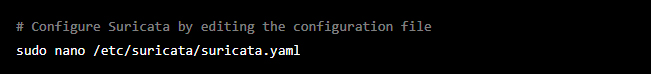
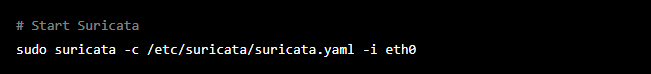
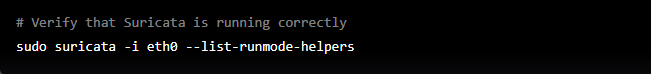
Cybercrime is a type of criminal activity that uses computers, networks, or connected devices as a tool to commit illegal acts. It can be done by individuals or groups and can have many different forms. Some examples include hacking into computers and networks to steal sensitive information, spread malware, or cause damage. It can also include activities like online fraud, identity theft, and illegal online activities like distributing child pornography. Because of the widespread use of technology, cybercrime is a growing concern worldwide, and it’s essential to protect our online information and devices from cybercriminals.
We are going to discuss some useful tools that are commonly used by penetration testers and ethical hackers. These tools are part of a software called Kali Linux, which is used to test the security of different computer systems. Before diving into the list of tools, let’s go over some important terms related to the topic.
What Is Penetration Testing?
Penetration testing, also known as pen testing, is a simulated cyber attack against a computer system to check for exploitable vulnerabilities. The goal of this ethical hacking is to help organizations locate weaknesses in their network infrastructure and guide efforts to increase security. Pen testers use the same tools and techniques as attackers to find and demonstrate the potential impacts of weaknesses in a system. They can examine whether a system is robust enough to withstand attacks from different positions and roles. Insights from the pen test can be used to fine-tune security policies and patch vulnerabilities.
- Penetration testing, also called pen testing, is a simulated cyber attack against a computer system to check for exploitable vulnerabilities.
- It is an ethical, or white hat, hacking method that helps organizations identify weaknesses in their network infrastructure and guide efforts to increase security.
- Pen testers use the same tools, techniques, and processes as attackers to find and demonstrate the potential impacts of weaknesses in a system.
- They can examine whether a system is robust enough to withstand attacks from different positions and roles.
- Insights from the pen test can be used to fine-tune security policies and patch vulnerabilities.
- Pen testing can involve the attempted breaching of any number of application systems, (e.g., application protocol interfaces (APIs), frontend/backend servers) to uncover vulnerabilities, such as unsanitized inputs that are susceptible to code injection attacks.
- It can also be used to augment a web application firewall (WAF) by providing insights on fine-tuning security policies and patching detected vulnerabilities.
- The fundamental purpose of penetration testing is to measure the feasibility of systems or end-user compromise and evaluate any related consequences such incidents may have on the involved resources or operations.
What Is Kali Linux?
Kali Linux is an open-source distribution designed specifically for cybersecurity professionals, ethical hackers, and penetration testers. It is based on Debian and includes over 600 tools for penetration testing and security auditing. The distribution is actively developed by Offensive Security, and is one of the most popular security distributions used by ethical hackers and infosec companies.
- Kali Linux is not designed for general use, but for professionals and web admins who know how to run it.
- Kali Linux includes a wide range of tools for exploitation, forensic, hardware hacking, information gathering, password cracking, reverse engineering, wireless attacks, web applications, stress testing, sniffing and spoofing, vulnerability analysis and more.
- Kali Linux is a multi-platform solution, accessible and freely available to information security professionals and hobbyists.
- Kali Linux is completely free of charge and always will be, with open source development model and the development tree available for all to see.
- Kali Linux is FHS compliant, supports wide-ranging wireless device, custom patched kernel for injection, developed in a secure environment, GPG signed packages and repositories, multi-language support, and is completely customizable to suit specific needs.
1. Fluxion
Fluxion is a tool used by cybersecurity professionals and penetration testers to test the security of Wi-Fi networks. It is designed to find vulnerabilities in both personal and corporate networks by using a technique called a Man-in-the-Middle (MITM) attack. Unlike other Wi-Fi cracking tools, Fluxion does not use time-consuming brute force methods.
- Fluxion uses a technique called social engineering to trick users on the targeted network into revealing their Wi-Fi password.
- It creates a fake access point that looks like the legitimate one, and then prompts users to enter their password when they try to connect to it.
- The tool then captures and reports the password to the pen tester, allowing them to gain access to the network.
- Fluxion is compatible with the latest version of Kali Linux, which is a popular operating system for penetration testing.
- It is a sophisticated tool that requires a certain level of technical knowledge to use effectively. It is not recommended for casual or inexperienced users.
Fluxion is a powerful tool that can be used to identify vulnerabilities in wireless networks. It is a valuable tool for cybersecurity professionals, penetration testers, and other experts who need to assess the security of Wi-Fi networks. It helps them to find weaknesses in the network and to develop strategies to protect against potential attacks.
2. John the Ripper
John the Ripper is a free, open-source password security testing and recovery tool that works on multiple platforms including Linux, Windows, macOS, and Unix. It can launch brute force attacks to test the strength of system passwords and can also test encryptions like DES and SHA-1. John the Ripper can be run automatically using crons, can be paused and resumed during scans, and allows for custom dictionary building and brute force rules. The “jumbo” version of John the Ripper has additional functionality and supports a wide range of hash and cipher types for various systems, applications, and networks. It is a popular tool for system administrators and security penetration testers to test the security of their organization’s passwords.
- Brute force testing: John the Ripper can launch brute force attacks to test the strength of system passwords by trying a large number of possible combinations.
- Dictionary attacks: John the Ripper can use a pre-defined list of words to try and match against the password, this is a common method of cracking passwords.
- Encryption testing: John the Ripper can test the strength of various encryption algorithms like DES and SHA-1.
- Password recovery: John the Ripper can be used to recover lost or forgotten passwords.
- Security auditing: John the Ripper can be used by system administrators and security professionals to perform security audits and identify vulnerabilities in password security.
3. Metasploit Framework
Metasploit Framework (MSF) is a powerful and widely used penetration testing tool that allows security professionals and ethical hackers to test for vulnerabilities and exploit them on remote systems. MSF is based on Ruby and is available for Windows and Linux. It includes a wide range of security tools that can be used for network enumeration, evading detection, exploit development and execution, scanning remote targets, and collecting valuable data.
MSF features include:
- Network enumeration and discovery
- Evading detection on remote hosts
- Exploiting development and execution
- Scanning remote targets
- Exploiting vulnerabilities and collecting valuable data
The Metasploit Project is owned by Rapid7, a US-based cybersecurity company. The Metasploit Framework is the most notable sub-project of the Metasploit Project, it is open-source and it contains a suite of tools that you can use to test security vulnerabilities, enumerate networks, execute attacks, and evade detection. It also includes anti-forensic and evasion tools.
The main usage of Metasploit Framework are:
- Penetration Testing: It can be used for testing security vulnerabilities and exploiting them on remote systems
- Exploit Development: It can be used for developing and testing exploit codes
- Network Enumeration: It can be used for discovering and enumerating networks
- Evasion: It can be used for evading detection by security systems
- Data Collection: It can be used for collecting valuable data from the target systems
Due to its wide range of applications, Metasploit Framework is used by everyone from the evolving field of DevSecOps professionals to hackers. It is an open-source tool that can be easily customized, and can be used with most operating systems. It includes more than 1677 exploits and nearly 500 payloads, which can be used to evade antivirus software and take over sessions or upload and download files. The framework is popular with hackers and widely available, which reinforces the need for security professionals to become familiar with it.
4. Lynis
Lynis is a powerful, open-source cybersecurity tool that is used for compliance testing, system auditing, and hardening. It can be used for vulnerability scanning and penetration testing as well. Lynis is available for multiple platforms including Linux, macOS, BSD, and AIX. It runs over 300 security tests on the remote host and provides an output report which includes suggestions, warnings, and any critical security issues that were found on the machine.
The main features of Lynis include:
- It is open source and free, with commercial support available.
- It is simple to install from the Github repository.
- It can run on multiple platforms.
- It can run up to 300 security tests on the remote host.
- The output report is shared on-screen and includes suggestions, warnings, and any critical security issues found on the machine.
The main usage of Lynis are:
- Security Auditing: Lynis performs an in-depth security scan and runs on the system itself. The primary goal is to test security defenses and provide tips for further system hardening.
- Compliance testing: Lynis can be used for compliance testing such as PCI, HIPAA, SOx and others.
- System Hardening: Lynis can be used for system hardening. It scans for general system information, vulnerable software packages, and possible configuration issues.
- Vulnerability scanning: Lynis can be used to scan for vulnerabilities on a system.
- Penetration testing: Lynis can be used by penetration testers to assess the security defenses of their systems.
5. Nmap
Nmap (Network Mapper) is a free and open-source tool used for vulnerability checking, port scanning, and network mapping. It was created in 1997 and is widely considered the gold standard for network scanning tools. It is used by network administrators to detect devices currently running on the system, the port numbers by which the devices are connected, open ports, and services on a network. Nmap allows to discover active hosts within any network and gain additional information related to penetration testing, such as existing open ports, OS detection, app version detection, and scriptable interaction. It is also highly customizable and can be modified to work within most customized or specialized environments. It is available in C, C++, Perl and Python, and support a wide range of operating systems.
Some advantages of Nmap include:
- Host discovery, which identifies hosts in any network
- Port scanning which lets you enumerate open ports on either a local or remote host
- OS detection which helps gather operating system and hardware information about any connected device
- App version detection which lets you determine the application name and version numbers
- Scriptable interaction which extends the Nmap default capabilities by using the Nmap Scripting Engine (NSE)
- Support for Windows, Mac, Linux and other operating systems.
- Ability to quickly recognize all the devices including servers, routers, switches, mobile devices, etc on single or multiple networks
- Helps identify services running on a system including web servers, DNS servers, and other common applications
- Can detect application versions with reasonable accuracy to help detect existing vulnerabilities
- Use during security auditing and vulnerability scanning to attack systems using existing scripts
6. Nikto
Nikto is an open-source web server scanner that performs comprehensive tests against web servers for multiple items, including over 6700 potentially dangerous files and programs, checks for outdated versions of over 1250 servers, and version-specific problems on over 270 servers. It also checks for server configuration items such as the presence of multiple index files, HTTP server options, and will attempt to identify installed web servers and software. It is written in Perl and features support for host-based authentication, proxies, SSL encryption, and more. It can output results in various formats such as TXT, XML, HTML, NBE, or CSV and it is frequently updated.
Some advantages of Nikto include:
- Scanning multiple ports on a server
- Providing IDS evasion techniques
- Apache and cgiwrap username enumeration
- Identifying installed software via headers, files, and favicons
- Checks for outdated server components
- Scan multiple ports on a server, or multiple servers via input file (including nmap output)
- Subdomain guessing
- Mutation techniques to “fish” for content on web servers
- Scan tuning to include or exclude entire classes of vulnerability checks
- Guess credentials for authorization realms
- Enhanced false positive reduction via multiple methods
- Proxy support (with authentication)
- Cookies support.
7. Skipfish
Skipfish is an active web application security reconnaissance tool that is used for information gathering and testing the security of websites and web servers. It prepares an interactive sitemap for the targeted site by carrying out a recursive crawl and dictionary-based probes. The resulting map is then annotated with the output from a number of active security checks. The final report generated by the tool is meant to serve as a foundation for professional web application security assessments. It is a free, open-source tool that is available on GitHub and can be used by security researchers. Some of the key features of Skipfish include automated learning capabilities, differential security checks, ease of use, a low false positive ratio, and the ability to run high-speed security checks with over 200 requests per second. It supports Kali Linux, FreeBSD, MacOS X and Windows (Cygwin) environments.
Some advantages of Skipfish include:
- Automated learning capabilities: Skipfish has the ability to adapt to different web frameworks and technologies, making it a versatile tool for web application security assessments.
- Differential security checks: Skipfish performs a range of security checks that are designed to detect subtle flaws, helping to identify vulnerabilities that may be missed by other tools.
- High speed: Skipfish is written in C, which makes it highly optimized for HTTP handling and low on CPU usage, allowing for high-speed security checks.
- Ease of use: Skipfish is user-friendly and includes features such as on-the-fly wordlist creation and form autocompletion to make it easy for users to perform web application security assessments.
- Open-source and free: Skipfish is a free and open-source tool that can be used by security researchers and professionals, making it accessible to a wide range of users.
8. Social Engineering Toolkit
The Social-Engineer Toolkit (SET) is an open-source Python-based penetration testing framework designed for social engineering attacks. It is commonly used by security researchers and penetration testers to check for cybersecurity flaws in systems. SET offers various attack vectors such as spear-phishing attacks, website attacks, and an Infection Media Generator. It also supports integration with third-party modules and can run on Linux, Unix, and Windows. SET is already installed in Kali Linux and it can also be downloaded and installed from Github. It is a product of TrustedSec, LLC and has over 2 million downloads.
List of Five advantages
- The Social Engineering Toolkit is an open-source Python-based penetration testing framework that helps launch social-engineering attacks.
- It supports a wide range of attack vectors such as Wi-Fi AP-based attacks, SMS and email attacks, web-based attacks and creation of payloads.
- It is a multi-platform tool and can be run on Linux, Unix, and Windows.
- It allows for integration with third-party modules and includes access to the Fast-Track Penetration Testing platform.
9. Burp Suite
Burp Suite is a popular software tool used for web application security testing. It acts as a proxy and allows users to make changes to requests, making it useful for testing vulnerabilities such as XSS and SQLi. Kali Linux comes with the community edition of Burp Suite, which is free to use. However, there is also a paid version called Burp Suite Professional that has more features. To use Burp Suite, one must first set it up and then turn on the interceptor in the Proxy tab. After that, requests can be captured and analyzed by visiting any URL. Burp Suite is an integrated platform that works seamlessly to support the entire testing process from initial mapping to finding and exploiting security vulnerabilities. It is written in Java and developed by PortSwigger Web Security. It has three editions Community, Professional, Enterprise.
List of Burp Suite main features
- Proxy: Allows for intercepting and modifying requests between the browser and the web server.
- Spider: Automatically crawls a website and creates a map of all URLs and content.
- Scanner: Identifies vulnerabilities in the web application, such as SQL injection or cross-site scripting.
- Intruder: Allows for manual manipulation of requests to test for vulnerabilities.
- Repeater: Allows for editing and re-sending individual requests for further testing.
- Sequencer: Analyzes randomness and predictability of session tokens to test for weak session management.
- Extender: Enables integration with third-party plugins and tools.
- Comparer: Allows for comparing and analyzing differences in requests and responses.
- Decoder: Decodes and encodes data in various formats to test for encoding-related vulnerabilities.
Cybersecurity is a growing field with a high demand for skilled professionals. A career in cybersecurity offers the opportunity to make a positive difference, be well compensated, and have sustained demand for years to come. Hackzone Cyber Security offers comprehensive training in areas such as risk analysis and mitigation, cloud-based security, and compliance. Cybersecurity experts can earn an annual average of $79,774 in the United States and ₹783,000 in India. Job roles in this field include Security Analyst, Security Engineer, Ethical Hacker, Intrusion Detection Specialist, and more. One can also achieve certifications to stand out in the field and receive a pay raise.