- A cybersecurity corporation focuses on acquiring and trading undisclosed software vulnerabilities (zero-day exploits).
- Recent headline: Corporation offering a remarkable $20 million to security researchers for crafting advanced hacking tools for breaching iPhones and Android devices.
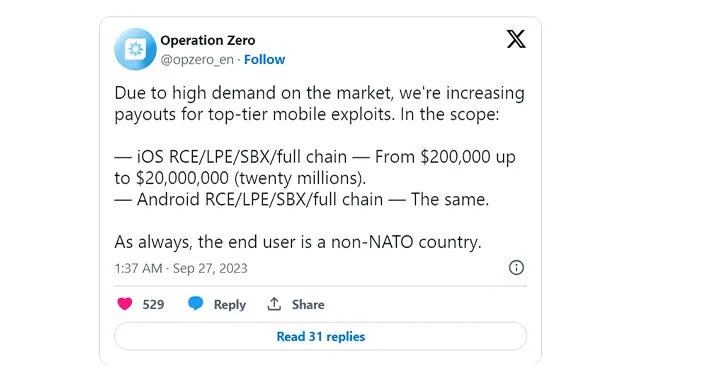
- Announcement: “Operation Zero” proclaimed the increased incentive, raising zero-day exploit rewards from $200,000 to $20 million.
- Objective: Encourage development teams to actively engage with their innovative platform through competitive arrangements and supplementary rewards.
- Origin: Established in Russia in 2021, targeting end users in non-NATO nations exclusively.
- CEO’s stance: Guarded about targeting non-NATO nations, hinting at strategic reasoning without elaboration.
- Market dynamics: Suggested the $20 million rewards could be temporary, reflecting the complex nature of hacking into iOS and Android platforms.
- Valuation of exploits: Highly influenced by availability in the zero-day marketplace, particularly targeting comprehensive mobile device exploitation techniques.
- Unique approach: Divergence from traditional bug bounty platforms by not notifying vendors, instead selling to discerning government clients.
- Clandestine market: Operates in secrecy with fluctuating prices and undisclosed customer identities.
- Publicized price lists: Operation Zero disclosed their pricing, offering insight into the enigmatic world of cybersecurity deals.
